Information Security has become a business-critical topic in recent times, especially for businesses whose operations are dependent on IT. An existing customer of Lakana aimed to build a reputation for maintaining high standards in information security. It set itself the goal of achieving a range of certifications relevant to its business and customers. Lakana was asked to manage the company’s information security management (ISM) program.
Lakana designed a core ISM management process matching the requirements and culture of the customer’s organization. The cyclic process defined four steps: requirements, implementation, operation and control.
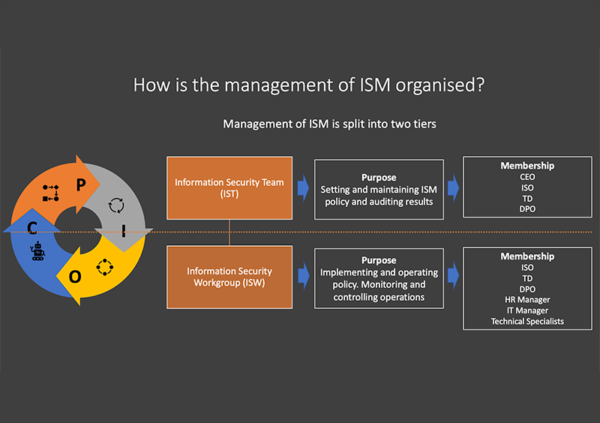
“Lakana has the unique capability to combine strategic consultancy thinking with a hands-on implementation force.”
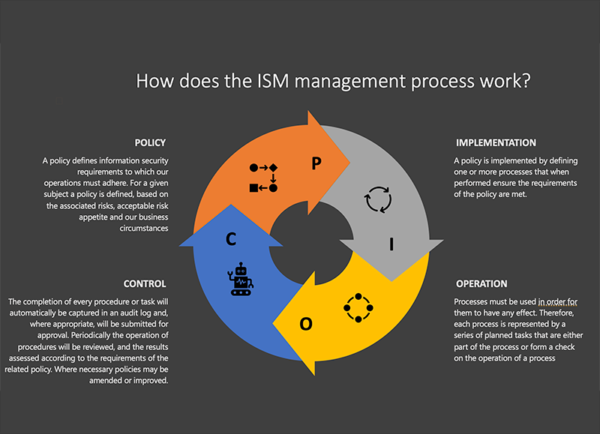
Requirements are expressed as the organization’s ISM policies. Procedures describe how ISM is implemented within the company. Operation of the procedures is captured in scheduled tasks. A formal approvals process ensures that the results of tasks are assessed and controlled. Lessons learned are fed back into policy improvements. The ISM management process has been implemented with Microsoft Teams, ensuring that all ISM information is suitably available, controlled and audited according to the relevant standards. With their ISM management process now in place, the company is proceeding with the development of policies, procedures and tasks. In parallel the company’s staff will be introduced to ISM and involved in its further development and deployment. Lakana continues to support the customer’s information security management program.
